- Pro
- Security
Dynamic evasion techniques make analysis difficult while malware executes undetected
Comments (0) ()When you purchase through links on our site, we may earn an affiliate commission. Here’s how it works.
 (Image credit: Shutterstock/supimol kumying)
(Image credit: Shutterstock/supimol kumying)
- Fake Windows updates deliver advanced malware hidden inside encrypted PNG images
- Hackers trick victims with update screens that secretly execute malicious commands
- Stego Loader reconstructs dangerous payloads entirely in memory using C# routines
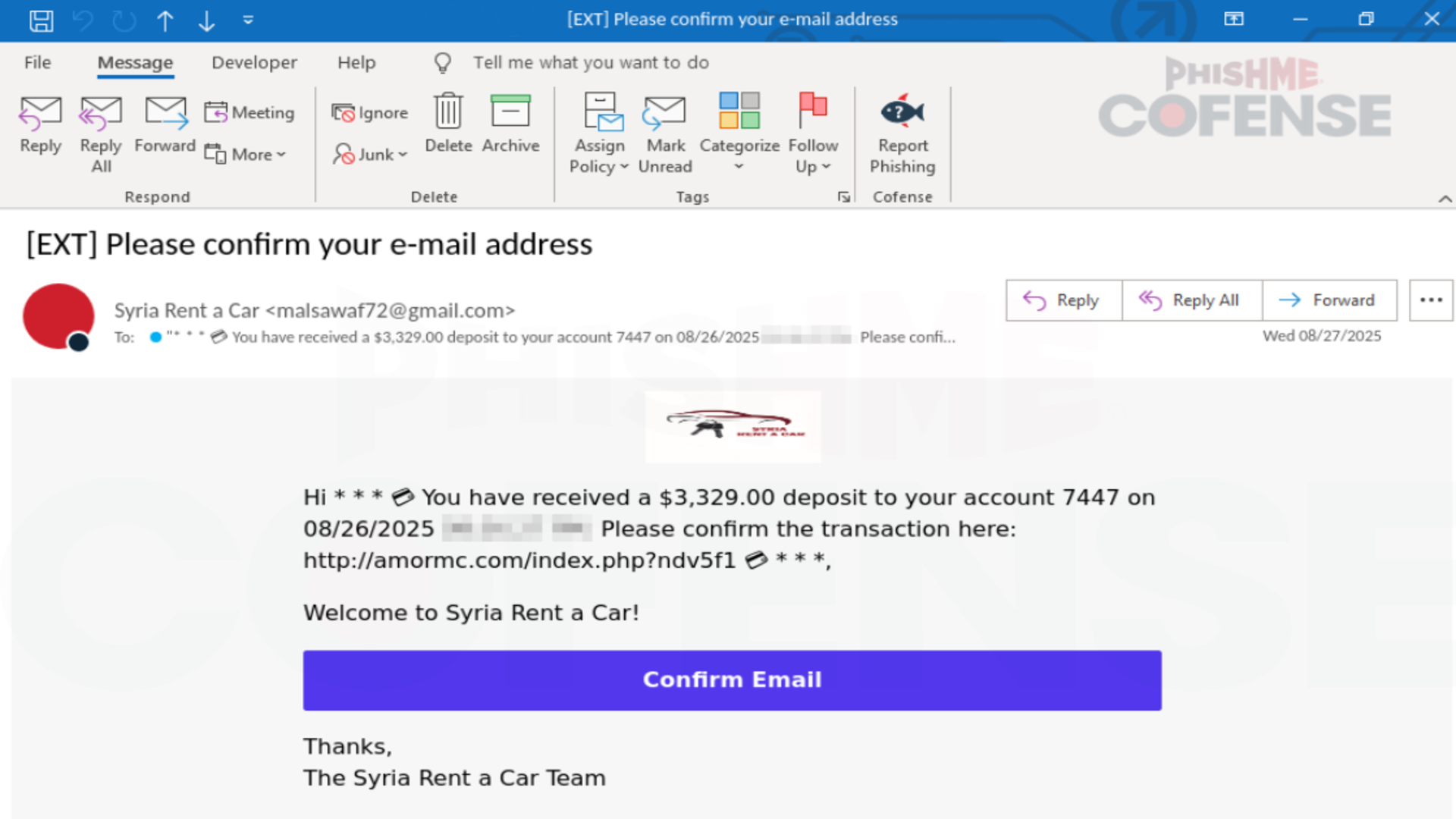
Hackers are increasingly using fake Windows Update screens to distribute complex malware through social engineering tactics.
ClickFix attacks convince users to execute commands in Windows by mimicking legitimate update prompts in full-screen web browser pages, Huntress researchers Ben Folland and Anna Pham found.
- Amazon Black Friday deals are live: here are our picks!
The experts reported that in some instances, attackers instruct victims to press specific keys, which automatically paste malicious commands into the Windows Run box.
You may like-
 Fake VPN checker tool lets hackers bypass antivirus protections
Fake VPN checker tool lets hackers bypass antivirus protections
-
 Microsoft's branding power is being used by criminals to funnel victims to tech support scam centers - here's what you need to know
Microsoft's branding power is being used by criminals to funnel victims to tech support scam centers - here's what you need to know
-
 TikTok videos used to hide dangerous malware attacks - here's how to stay safe
TikTok videos used to hide dangerous malware attacks - here's how to stay safe
Steganography and multi-stage payloads
These commands then trigger malware execution, bypassing standard system protections and affecting both individual and enterprise systems.
The malware payloads are hidden using steganography inside PNG images, encrypted with AES, and reconstructed by a .NET assembly called Stego Loader.
This loader extracts the shellcode using custom C# routines and repacks it with the Donut tool, allowing execution of VBScript, JScript, EXE, DLL files, and .NET assemblies entirely in memory.
Analysts identified the resulting malware as variants of LummaC2 and Rhadamanthys.
Are you a pro? Subscribe to our newsletterContact me with news and offers from other Future brandsReceive email from us on behalf of our trusted partners or sponsorsBy submitting your information you agree to the Terms & Conditions and Privacy Policy and are aged 16 or over.The use of steganography in these attacks demonstrates that malware delivery is moving beyond traditional executable files, creating a new challenge for threat detection and incident response teams.
Attackers also implement dynamic evasion tactics such as ctrampoline, which calls thousands of empty functions to make analysis more difficult.
One variant using the fake Windows Update lure was detected in October 2025, and law enforcement disrupted part of its infrastructure through Operation Endgame in November.
You may like-
 Fake VPN checker tool lets hackers bypass antivirus protections
Fake VPN checker tool lets hackers bypass antivirus protections
-
 Microsoft's branding power is being used by criminals to funnel victims to tech support scam centers - here's what you need to know
Microsoft's branding power is being used by criminals to funnel victims to tech support scam centers - here's what you need to know
-
 TikTok videos used to hide dangerous malware attacks - here's how to stay safe
TikTok videos used to hide dangerous malware attacks - here's how to stay safe
This prevented the final payload from being delivered via malicious domains, although the fake update pages remain active.
The attacks continue to evolve, alternating between human verification prompts and update animations to trick users into executing commands.
The researchers recommend monitoring process chains for suspicious activity, such as explorer.exe spawning mshta.exe or PowerShell.
Investigators can also review the RunMRU registry key for executed commands.
Organizations are advised to combine malware removal practices with antivirus scanning and firewall protection to limit exposure.
Disabling the Windows Run box, where feasible, and carefully inspecting image-based payloads are additional recommended precautions.
Enterprises must account for risks that arise from legitimate-looking assets, such as images and scripts, being weaponized, which complicates logging, monitoring, and forensic analysis.
This also raises concerns about supply chain security and the potential for attackers to exploit trusted update mechanisms as entry points.
Follow TechRadar on Google News and add us as a preferred source to get our expert news, reviews, and opinion in your feeds. Make sure to click the Follow button!
And of course you can also follow TechRadar on TikTok for news, reviews, unboxings in video form, and get regular updates from us on WhatsApp too.
 Efosa UdinmwenFreelance Journalist
Efosa UdinmwenFreelance JournalistEfosa has been writing about technology for over 7 years, initially driven by curiosity but now fueled by a strong passion for the field. He holds both a Master's and a PhD in sciences, which provided him with a solid foundation in analytical thinking.
You must confirm your public display name before commenting
Please logout and then login again, you will then be prompted to enter your display name.
Logout Read more Fake VPN checker tool lets hackers bypass antivirus protections
Fake VPN checker tool lets hackers bypass antivirus protections
 Microsoft's branding power is being used by criminals to funnel victims to tech support scam centers - here's what you need to know
Microsoft's branding power is being used by criminals to funnel victims to tech support scam centers - here's what you need to know
 TikTok videos used to hide dangerous malware attacks - here's how to stay safe
TikTok videos used to hide dangerous malware attacks - here's how to stay safe
 Experts warn ClickFix malware attacks are back, and more dangerous than ever before - here's how to stay safe
Experts warn ClickFix malware attacks are back, and more dangerous than ever before - here's how to stay safe
 Criminals are using AI-generated fake copyright violation threats to take over social media and websites - here's what you need to know
Criminals are using AI-generated fake copyright violation threats to take over social media and websites - here's what you need to know
 Windows Server flaw targeted by hackers to spread malware - here's what we know
Latest in Security
Windows Server flaw targeted by hackers to spread malware - here's what we know
Latest in Security
 Malicious Blender model files deliver StealC infostealing malware
Malicious Blender model files deliver StealC infostealing malware
 Popular JavaScript library can be hacked to allow attackers into user accounts
Popular JavaScript library can be hacked to allow attackers into user accounts
 This devious botnet tried a trial run during the recent AWS outage - so when will it be back?
This devious botnet tried a trial run during the recent AWS outage - so when will it be back?
 Asahi confirms cyberattack leaked data on 1.5 million customers
Asahi confirms cyberattack leaked data on 1.5 million customers
 New macOS malware chain could cause a major security headache - here's what we know
New macOS malware chain could cause a major security headache - here's what we know
 Ransomware hackers attack SMBs being acquired to try and gain access to multiple companies
Latest in News
Ransomware hackers attack SMBs being acquired to try and gain access to multiple companies
Latest in News
 NYT Connections hints and answers for Friday, November 28 (game #901)
NYT Connections hints and answers for Friday, November 28 (game #901)
 NYT Strands hints and answers for Friday, November 28 (game #635)
NYT Strands hints and answers for Friday, November 28 (game #635)
 Quordle hints and answers for Friday, November 28 (game #1404)
Quordle hints and answers for Friday, November 28 (game #1404)
 Marvel Rivals is having a Black Friday Blowout to celebrate the game's first anniversary – here's how it works
Marvel Rivals is having a Black Friday Blowout to celebrate the game's first anniversary – here's how it works
 Sony A7 V leak gives us our first glimpse of imminent flagship camera
Sony A7 V leak gives us our first glimpse of imminent flagship camera
 Dell paints bleak picture of Windows 11's lack of popularity at End of Life
LATEST ARTICLES
Dell paints bleak picture of Windows 11's lack of popularity at End of Life
LATEST ARTICLES- 1Malicious Blender model files deliver StealC infostealing malware
- 2Missouri to enforce mandatory age verification in three days
- 3NYT Connections hints and answers for Friday, November 28 (game #901)
- 4NYT Strands hints and answers for Friday, November 28 (game #635)
- 5Quordle hints and answers for Friday, November 28 (game #1404)




